The Heartbleed Vulnerability is a serious SSL Bug that basically can allow a hacker to decrypt your SSL traffic. Network and Systems teams are racing to resolve vulnerabilites to their applications. I’ll focus on the impact to IIS hosted applications.
Does Heartbleed affect IIS SSL traffic? The short answer is no. The Windows Operating Systems use the Microsoft Schannel Provider to implement SSL, not OpenSSL. See the following MSDN link to see the list of cipher suites. But your application could still be vulnerable if your servers are behind a load balancer or Proxy Server and SSL is terminated at that device not IIS. Most load balancers and proxy servers are linux based and implement OpenSSL. F5 Local Traffic Managers are an example of this. If your running an F5 LTM make sure you review SOL15159.
How to Check Your Cipher Suite
If you need to determine what cipher suite your application is using, you can do that fairly easy using Network Monitor.
- Open Network Monitor and start a capture.
- On the same machine access the website in question using IE or any other browser over SSL. Stop the capture.
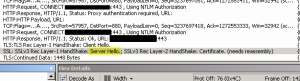 Look for the Server Hello packet, this is where the server will set the Cipher Suite to be used.
Look for the Server Hello packet, this is where the server will set the Cipher Suite to be used.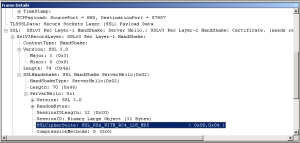 In the frame details drill into the SSL details, find the SSLHandshake, and then find the SSLCipherSuite. The Cipher Suite used will help you determine what SSL Provider was used on the server. The Cipher suite to the left came from an F5 OpenSSL provider.
In the frame details drill into the SSL details, find the SSLHandshake, and then find the SSLCipherSuite. The Cipher Suite used will help you determine what SSL Provider was used on the server. The Cipher suite to the left came from an F5 OpenSSL provider.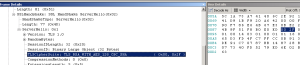 An IIS Cipher Suite will look similar to this. See the list of Windows Cipher Suites below.
An IIS Cipher Suite will look similar to this. See the list of Windows Cipher Suites below.- This is not a guarantee that you are not using OpenSSL, it only tells you what cipher suite is being used.
SChannel Cipher Suites
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P256
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P384
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
TLS_DHE_DSS_WITH_AES_128_CBC_SHA
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
TLS_DHE_DSS_WITH_AES_256_CBC_SHA
TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA
TLS_RSA_WITH_RC4_128_MD5
SSL_CK_RC4_128_WITH_MD5
SSL_CK_DES_192_EDE3_CBC_WITH_MD5
TLS_RSA_WITH_NULL_SHA256
TLS_RSA_WITH_NULL_SHA