Managing User Rights Assignments in Powershell
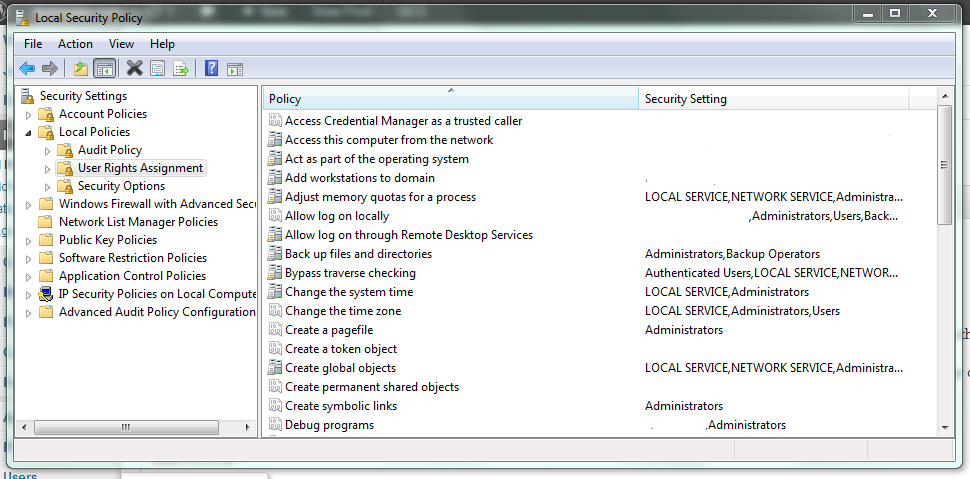
Windows User Rights, also known as Windows Privileges, are traditionally managed via GPO or in the simplest of cases via the server’s Local Security Policy. These assignments control special permissions that are often needed by IIS applications or other application hosting on Windows Servers.
So how can we manage these assignments in Powershell? There’s no obvious solution provided in Powershell, but there are several options are available. None of which are a pure Powershell solution, but some are close.
- Wrap the ntrights.exe process in Powershell. This is relatively simple, but the downside is having an external dependency on the ntrights.exe file.
- Embed a wrapper class to the LSA API in your script. This is a pretty good solution but certainly bloats your script.
- Load and Reference the Carbon DLL (If you haven’t already checked out this Powershell library, you should it is very powerful and regularly updated. I choose this approach because it keeps the script clean and compact, it returns an array of strings for easy interrogation. It does require a dependency on carbon.dll, but this library provides a ton of functionality beyond just this.
I like the 3rd option, its very clean, and I like working with the Carbon library.
Example Script
param (
[Parameter(Mandatory=$true)]
[string]$identity,
[Parameter(Mandatory=$true)]
[string]$privilege,
[Boolean]$grant)
# Path to Carbon DLL
$CarbonPath = "\\ManagementServer\Store\Carbon.dll"
# Load Carbon Assembly
[Reflection.Assembly]::LoadFile($CarbonPath) | Out-Null
# Grant Privilege if flag is set
if ($grant){ [Carbon.Lsa]::GrantPrivileges( $Identity , $privilege )}
# Read Privileges
$result = [Carbon.Lsa]::GetPrivileges($Identity) | Where-Object { $_ -eq $Privilege }
# Display Output
if ($result -eq $null){
Write-Host "$identity does NOT have $privilege"
} else {
Write-Host "$identity has the $privilege"
}
Now lets take this script to the next level and wrap it into a DSC Script implementation. We can use this same logic in a DSC configuration to make sure our desired User Rights Assignments are kept in place.
DSC Example
$Identity = "domain\bpate"
$privilege = "SeServiceLogonRight"
$CarbonPath = "\\ManagementServer\Store\Carbon.dll"
Configuration WindowsPrivilegeExample
{
Node NodeName
{
Script Grant-SeServiceLogonRight
{
GetScript = {
[Reflection.Assembly]::LoadFile($CarbonPath) | Out-Null
$result = [Carbon.Lsa]::GetPrivileges($Identity) | Where-Object { $_ -eq $Privilege }
if ($result -eq $null) { return @{ Privilege = "Not Granted" }}
else { return @{ Privilege = "Granted" } }
}
TestScript = {
[Reflection.Assembly]::LoadFile($CarbonPath) | Out-Null
$result = [Carbon.Lsa]::GetPrivileges($Identity) | Where-Object { $_ -eq $Privilege }
return ($result -ne $null)
}
SetScript = {
[Reflection.Assembly]::LoadFile($CarbonPath) | Out-Null
[Carbon.Lsa]::GrantPrivileges( $Identity , $privilege )
}
}
}
}
What else can we do? We could also create a Custom DSC Resource to have a cleaner DSC Configuration.